To set up Okta SSO, follow the instructions below.
Content
- Requirements
- Supported Features
- Okta Configuration Steps
- Logging Into OpenPolicy Using Okta
1. Requirements
- Admin access to an Okta organization.
2. Supported Features
- Service Provider (SP)-Initiated Authentication (SSO) Flow: This authentication flow occurs when the user attempts to log in to the application from OpenPolicy.
- SCIM Provisioning
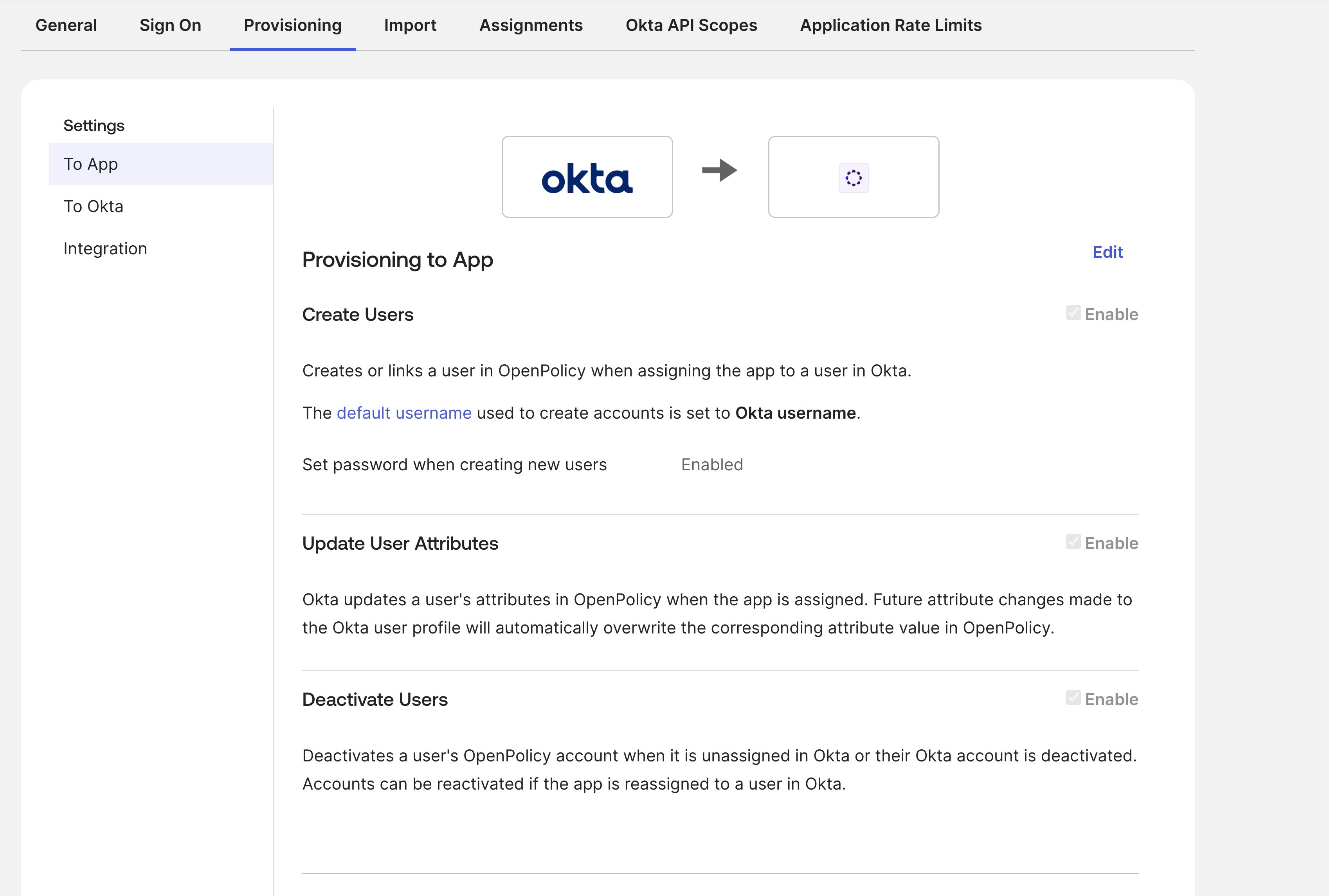
- Create Users
Users in Okta that are assigned to the OpenPolicy application in Okta are automatically added as members to your organization in OpenPolicy. - Deactivate Users
Users in Okta that are unassigned from the OpenPolicy application in Okta are automatically deleted as members to in organization in OpenPolicy. - Update User Attributes
Updating user information(e.g. first name, last name) on Okta would automatically reflect in the OpenPolicy application. - Import Users
This feature enables Okta to retrieve user accounts directly from OpenPolicy —either matching them with existing Okta profiles or creating new ones. Admins can initiate an import job, synchronize users into the Universal Directory, and review or confirm matches before onboarding. This feature facilitates scenarios where your app is a designated source of user records, allowing for seamless one-time or admin-triggered synchronization.
3. Okta Configuration Steps
- In Okta, navigate to Applications → Browse App Catalog, search for and add OpenPolicy.
During the installation you will be required to add a "subdomain" variable, please request it from OpenPolicy support.
,
- If you intend to use SCIM - make sure to go to "Provisioning" tab and check the boxes in this photo:
When using SCIM go to Provisioning->Integration
Go to "API Token" field and fill it in. you should receive it from OpenPolicy support.
Also, please ensure that the 'Import Groups' option located below the API token field is unchecked